Continuing the Hunt - Crypto 'Mining' Exposed Part II
Continuing the Hunt
Now that we have satisfied ourselves that this is not a legitimate cryptocurrency mining platform, we can tackle the rest of the investigation objectives set out in the first part of this series:
Is legitmining[.]website a legitimate cryptocurrency mining operation?- What other websites are linked to our target site?
- How long has the site been operational?
- Where is the site hosted?
- Who is responsible for the website?
Let’s start by trying to find other websites operated by the same people.
It is very typical for the same fraudsters to be running and managing multiple websites, each with their own twist on the same theme, sometimes targeted at specific geographic locations. A good place to start this phase is to try and identify what infrastructure the original target website is using. The infrastructure is likely to be shared across a number of different sites to reduce cost and simplify management of the various websites and services, just like a legitimate business.
Infrastructure DIGging
To find the apparent IP address of the server hosting the website you can use any number of online tools. For us a simple DNS lookup using the dig command will suffice for now.
dig +short legitmining.website
Pro Tip: Use the +short option to return the IP addresses from the DNS-A record and nothing else
The site has 2 valid IP addresses in the DNS-A record (i.e. the IP that browsers are directed to in order to recover the site content) - 172.67.221.139 - 104.21.25.10
But there’s a problem. Both IP addresses are provided by Cloudflare, forming part of their Content Delivery Network (CDN).
Cloudflare acts as a proxy between the true server for a website and external visitors, to provide protection against denial of service attacks and to help serve content more quickly, by hosting it on servers across the globe. However, this means that the actual IP address of the website is masked, only the proxy IP address is included in the DNS records.
Luckily for us, it is possible to discover the true IP address of a website behind Cloudflare, with a little patience, diligence and in some cases a bit of luck.
This excellent presentation by the esteemed @nixintel goes into some depth about multiple techniques that can help unmask servers hidden behind Cloudflare, this is highly recommended viewing.
Back to the Future

Historic DNS records are a quick way of identifying potential IP addresses for sites behind CloudFlare. As passive DNS services constantly scrape DNS records looking to associate domains to IP addresses they can catch sites that are temporarily hosted on their true IP address before they are put behind Cloudflare protection. If we query these services it could potentially lead to an IP address for our website.
Querying the PassiveTotal service from RiskIQ corroborates the same two IP addresses from our earlier dig command,
but on this occasion it doesn’t reveal any older IP addresses for our target website.
This is the reality of open source investigations. Not every technique will work every time, so it pays to have multiple ways of finding out the same information. So let’s move on to another technique.
Dare to Enumerate
In many cases, when a main website is safeguarded by Cloudflare, subdomains hosting supporting services like email or file transfer may remain vulnerable and unprotected. By conducting subdomain enumeration and resolving the IP address for each of these subdomains, we can capitalise on this oversight.
To find these subdomains we can use any subdomain enumeration tool such as subfinder, findomain or dnsdumpster.
The depth of your subdomain enumeration search will depend upon your specific use case. It is possible to use subfinder and findomain to brute-force subdomain enumeration, effectively using a wordlist to systematically search for valid DNS records for all possible subdomains.
In this case we can continue to use RiskIQ’s PassiveTotal to discover subdomains passively. If we don’t find anything useful via the passive method, then we can escalate up to a brute-force method.

Two subdomains stand out as worth further investigation: - mail.legitmining[.]website - webmail.legitmining[.]website
webmail.legitmining[.]website resolves to the same two Cloudflare IP addresses as the parent domain, so doesn’t take us any further forwards.
However, mail.legitmining[.]website is hosted at two new IPs: - 208.110.64.234 - 173.208.132.99
Both IPs are provided by the ISP ‘Wholesale Internet Inc’. Let’s take a look at what else is known to be hosted on these IPs and see if we can spot a theme…
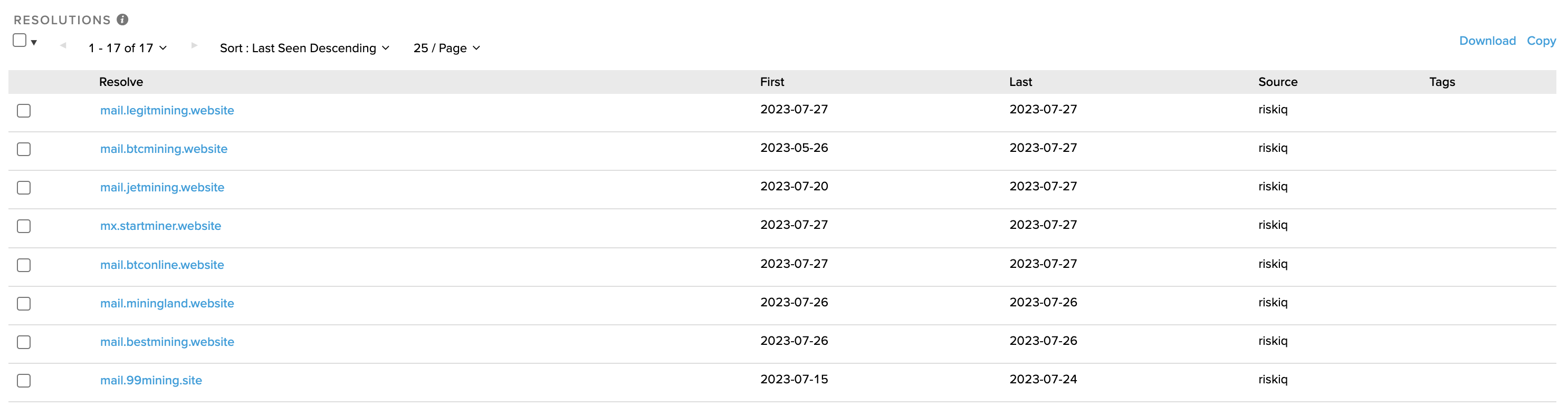
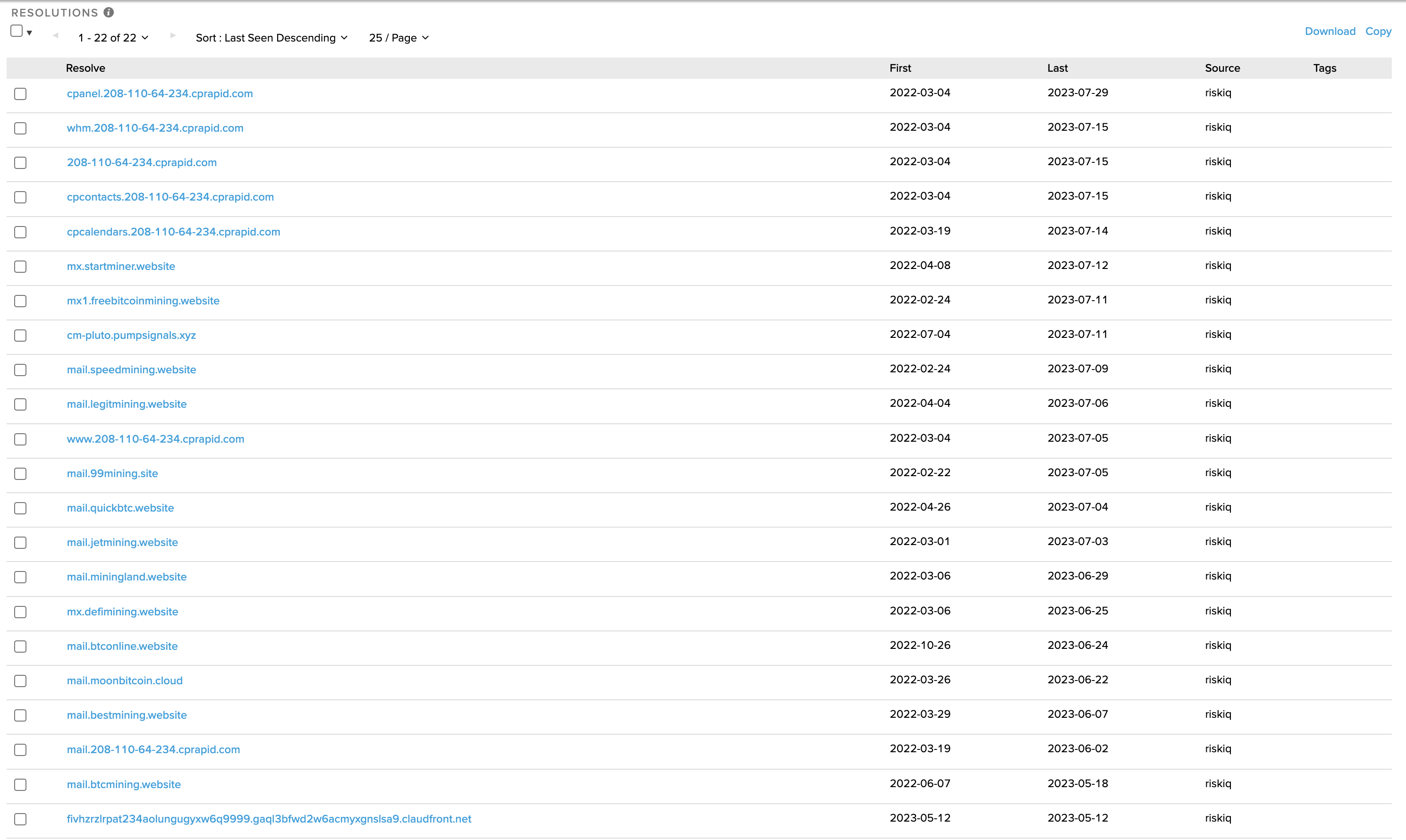
So it would appear that we have found our suspect’s infrastructure. The mail services of multiple crypto-mining themed websites are hosted on these two IPs.
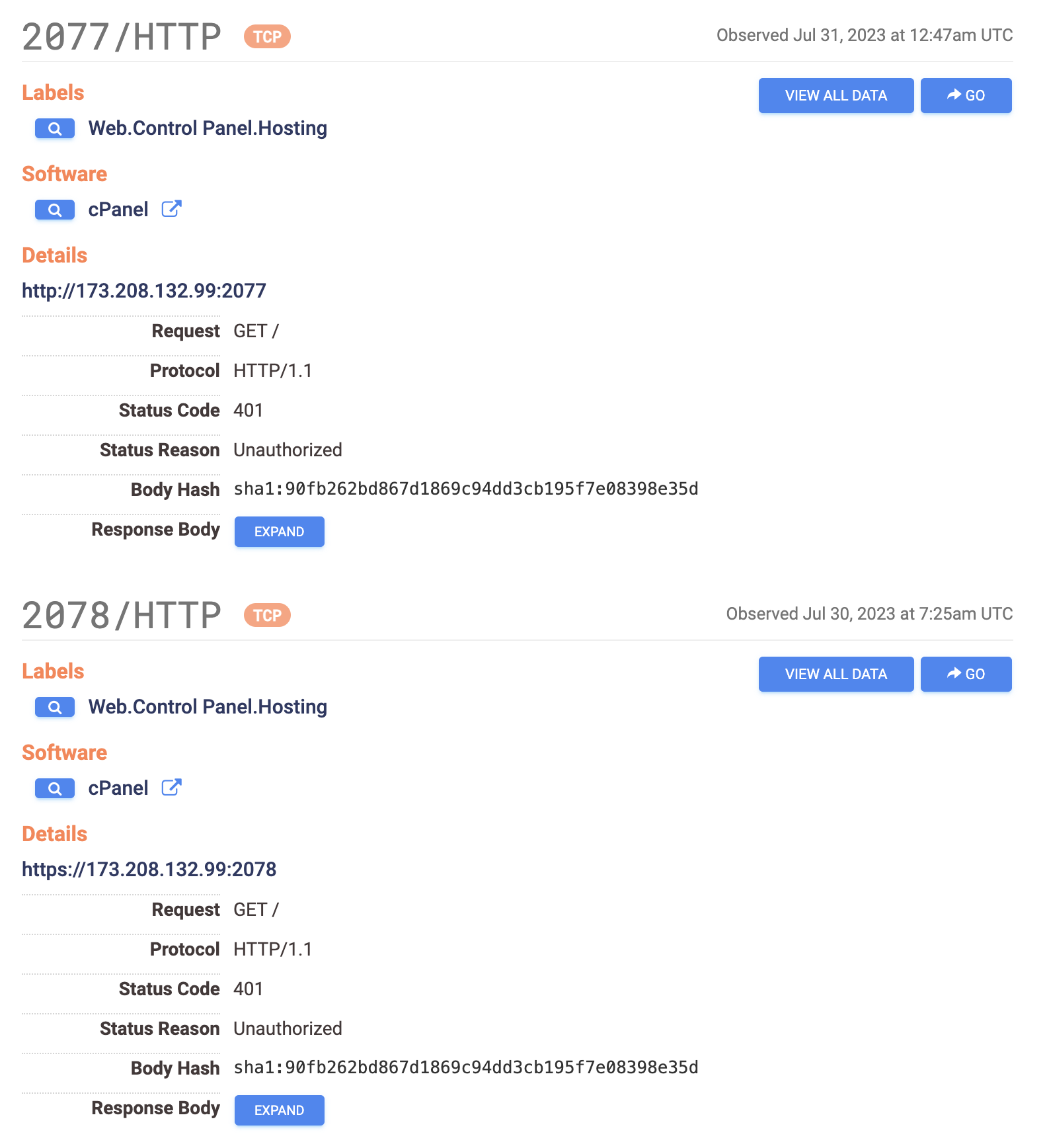
We can also see evidence of the common partnership of cPanel and WHM web hosting software. cPanel is used by end-users (website owners) to manage individual websites, and WHM is used by hosting providers or server administrators to manage multiple cPanel accounts on a server. This is how our suspects are managing multiple websites across their infrastructure.
To corroborate our findings we can check the IPs using Censys.io
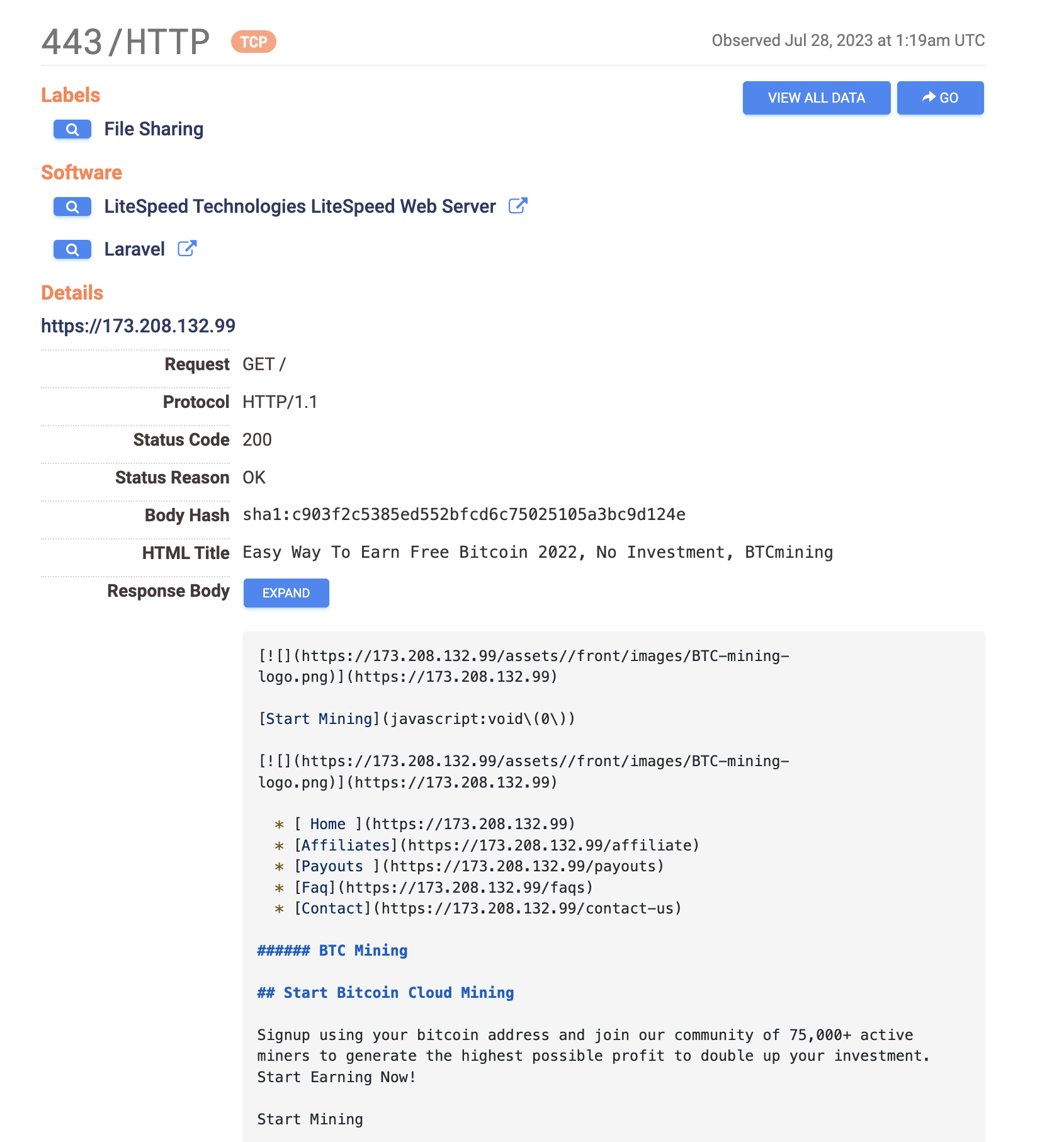
So the IP hosting mail.legitimining[.]website is also hosting btcmining[.]website amongst others. Censys also tells us that default ports for managing websites using cPanel are open on the same IP.
cURL to Confirm
To verify that this content is hosted at the suspect IP we can use curl --resolve to force a connection for a website from a specific IP, rather than the IP in our etc/hosts or from the IP in the DNS-A record.
curl https://www.btcmining.website --resolve www.btcmining.website:443:173.208.132.99
When this command returns the content you were expecting, then you have found the right IP address!

You Read the T&Cs, right?!?
Using some fairly basic techniques we have identified at least some of the IPs being used by our suspects to manage their various fraudulent websites. We can and will dig further but, if we were in a position to do so, we could now approach ‘Wholesale Internet Inc’ (WII) with the appropriate legal authority to request details of who is paying them to host these resources. Depending on the terms and conditions of the WII user agreement, we could also request that the websites hosted on these IPs be shut down for fraudulent activity.
Wouldn’t that feel nice?!
Thanks for reading (if you got this far). Next time we’ll look at some more advanced OSINT techniques to identify individuals linked to these websites. Stay tuned!
As always, feedback is much appreciated. Send it in to [email protected] or @ me on Elon’s hell site @webjitsu