Too Good To Be True- Crypto 'Mining' Exposed
Too Good To Be True? - Crypto ‘Mining’ Exposed
Part 1 of ? - My Gut Tells Me…
In the coming weeks I will be taking you along with me on an investigation into a potentially suspicious cryptocurrency mining website. Starting from a single website I will show how through (mostly) passive OSINT techniques we can gain valuable insights into how some cryptocurrency frauds operate, identify other websites potentially controlled by the same person(s) and look at bypassing measures that the fraudsters use to hide themselves.
We will use OSINT techniques such as public records searching, historic DNS records, passive reconnaissance tools and good old fashioned google-dorking to uncover the hidden infrastructure, history and methodology of our target.
Not everything we try will work but lessons will be learned and by the end of our investigation we will know much more about our target than we did at the start.
In the first part of the series we will focus on some fundamentals of OSINT investigations including ways to examining website content and leverage search engines to inform our investigation.
Before We Start - Identifying A Target
We all come into OSINT from different directions, with different perspectives, this is part of what makes OSINT such an interesting and constantly evolving area of research. Personally I come from a law enforcement background and my interest is in unmasking those who look to exploit and take advantage of others. So when choosing the target to sharpen my OSINT skills upon, I tend to focus on these type of companies and individuals. The unregulated cryptocurrency industry is a verdant orchard filled with shady characters, so let’s pick one and start there.
I used the UK Financial Conduct Authority list of Unregistered Cryptoasset Businesses to identify potential targets for further investigation. This is a list of “UK businesses that appear to be carrying on cryptoasset activity that are not registered with the FCA for anti-money laundering purposes” - it doesn’t mean that they are necessarily up to no good, they have not been convicted of any crime (as far as I know), but as you will see when we start to dig into the details, they may not be quite who or what they purport to be.
For this series of articles we will focus on www.legitmining[.]website - they are a reasonably recent addition to the FCA unregistered firms list and therefore their website and associated infrastructure is still likely to be operational. Also the fact that they have been added to the list means there is at least some suspicion that they are not entirely legitimate and quite frankly that is enough for me to take an interest and to start looking a little more closely.

N.B. There shouldn’t be any working links to their site in this article as I don’t want to link my site to theirs in any tangible way. Please do not visit them or any of the other target websites mentioned in these articles as it only increases their site traffic and boosts their seo rating.
We have ourselves a target website, so where do we start with our investigation?
What Is The Point?
First we need some objectives - what questions are we trying to answer?
Without clearly defined objectives our investigation could drift out of control with multiple lines of enquiry leading away into the distance with no idea of when and why to stop each one. In these circumstances it is very easy to get bogged down by the volume of data being collected, unable to decide which specific path of enquiries to go down, a situation known as analysis paralysis.
A clear set of objectives allows us to make reasoned decisions about what data is or is not relevant and use that to prioritise our next steps. It also provides us with a clear end-point. When we have either answered every question that we intended to, or exhausted all reasonable lines of enquiry to answer those questions then we have reached the end of our investigation.
Let’s set out our objectives at the beginning:
- Is legitmining[.]website a legitimate cryptocurrency mining operation?
- What other websites are linked to our target site?
- How long has the site been operational?
- Where is the site hosted?
- Who is responsible for the website?
These are all seemingly simple questions but they can be quite difficult to answer. For example, the first question has a direct yes or no answer, but to explain why we think it is one way or the other is more complex and will depend upon multiple competing factors. We may not even be able to answer all of these questions to a satisfactory standard, nevertheless, it is important to have this kind of focus and direction at the outset to prevent ourselves getting ‘analysis paralysis’ and coming to no conclusions at all.
What Do We Know?
A good habit in any investigation is to begin by writing down, in whatever format you are comfortable with, all the things you already know. From here you can decide how you are going to best answer the questions in your objectives, identify gaps in your knowledge and develop strategies to fill those knowledge gaps.
In this example we can look at our first source of information - the entry in the FCA list, which tells us the company name, address and website.
But what else can we determine beyond those obvious data points?
Well, we can tell that they have been operating inside the UK up to March 2022. We can tell that they have come to the attention of the FCA as a cryptoasset business. From the blurb on the FCA website we also know that they have failed to register themselves with the FCA, a process that requires an operator to provide evidence of how they are complying with anti-money laundering (AML) legislation and best practices.
Looking more closely at the url we can infer something else. To an old cynic like myself any website that has the word ‘legit’ in it is already ringing alarm bells. That the website operators saw fit to name their site ‘legitmining’ is a tacit admission that there are illegitimate mining services out there. Naming their site legitmining seeks to differentiate them from the bad eggs of the industry, but this type of overt and somewhat clumsy claim of legitimacy and trustworthiness is a warning sign. The double-bluff of legitmacy is a common tactic used by fraudsters, to act as a ‘white knight’ whilst picking the pocket of their victims. Just take a look at the example of fake fraud compensation firms, unfortunately this is not the last we will hear of this particularly cruel and opportunistic fraud type.
Now this suspicion is obviously not something we can rely on as a finding but it is important to take the human experience factor into consideration when conducting an investigation, as long as we are not led by it and any conclusions we draw are based upon facts and objective truths rather than suspicion and gut feeling.
Flying Visit
An obvious and necessary first step is to visit the website itself capture the content, how it behaves and find out what it can tell us. Whilst 90% of the techniques we will use in our investigation will be entirely passive, this stage is best done by actively connecting to the target site.
I’m not going to go into huge amounts of detail here about how to protect yourself when visiting a target site, there is already an abundance of good advice out there that can tell you how to do that (https://ssd.eff.org/), but I’ll summarise my approach with a few hard and fast rules: - Always use a VPN - Enable trusted browser security add-ons (e.g. Privacy Badger, CanvasBlocker, HTTPS Everywhere) - Try with a couple of different browsers as content may vary depending upon your browser (or use an user-agent switcher) - Visit once (per browser), capture everything you need, then stay away - If there is a passive way of getting the same information, do that instead
In a previous blog post I talked about the value of archiving for OSINT investigators and recommended a couple of tools to use for that job, singlefile and webrecorder.net.
As this is a dynamic site with interactive content we will use the webrecorder.net browser extension to create a visually identical and fully interactive archive of the target site that we can refer back to without having to visit the target site itself again.
The archive will serve as the source for our analysis of the content of the website, rather than making repeated visits to the original site, we can view and examine the archived version locally.
Too Good To Be True?
Let’s establish what services the website is offering and see if it helps to answer our first question, if the site is a legitimate cryptocurrency mining operation or not. To help us make a determination there are some key indicators of a crypto-mining scam to look out for: - inflated or impossible returns on investment - poor reputation and customer reviews - simulated trading or mining activity on the website - poorly worded or insufficiently detailed terms and conditions - use of central London office addresses
Immediately we are drawn to some rather grandiose claims about the scale of this mining operation.
Legitmining claim to be “one of the best leading cloud mining and hashing service providers in the world”. That poorly worded claim can be tested pretty easily.
Many mining pools include their identity in the blocks that they mine, permanently etching them into the blockchain itself, or they have well-known bitcoin public addresses. Blockchain.com have a series of charts which show the largest bitcoin mining pools based upon these identifiers. If legit mining are indeed “one of the best leading cloud mining and hashing service providers in the world” then they should be in there somewhere, right?
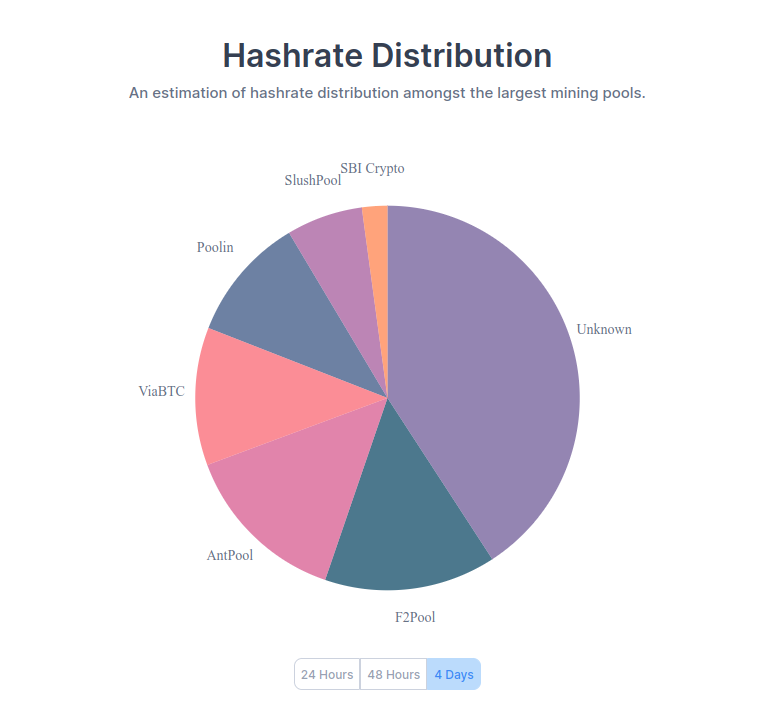
Maybe not…
They aren’t named in blockchain.com’s top mining pools but it is theoretically possible that they could be part of the large ‘Unknown’ sector in this chart. So instead we can do some google-dorking and take a look at the results.
Google FTW
| Search Term | Description |
|---|---|
| intext:“legitmining” | searches in website text for the exact phrase |
| intext:“legitmining” AROUND(3) “review” | searches for both exact phrases within 3 words of eachother in website text |
| “legitmining[.]website” -site:legitmining[.]website | searches the exact phrase but eliminates results from the target site |
We could include some keywords such as “fraud” or “scam” but beware of reinforcing cognitive bias by selectively searching for these types of loaded terms. I find it better to do a neutral search first and then add in these types of keywords at a later stage.
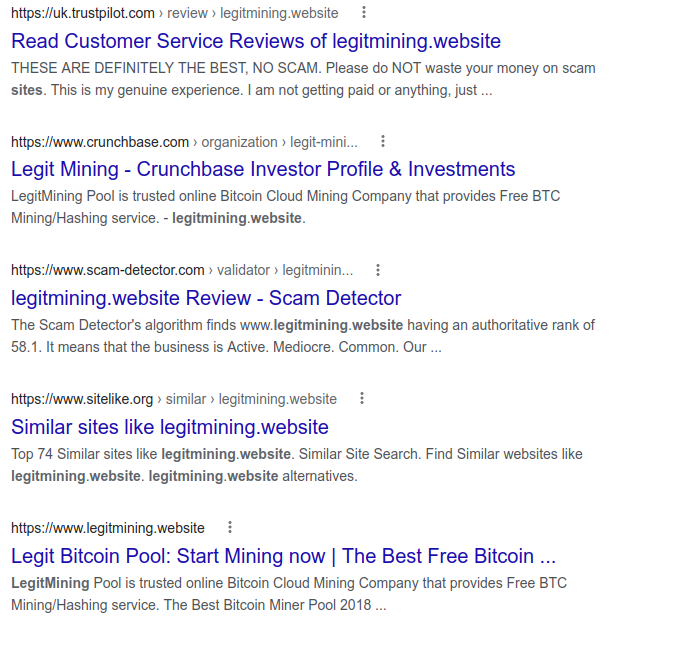
Our target website appears to have been featured on a number of review platforms and the reviews are not good. By ‘not good’ I mean ‘Cats’ not good.
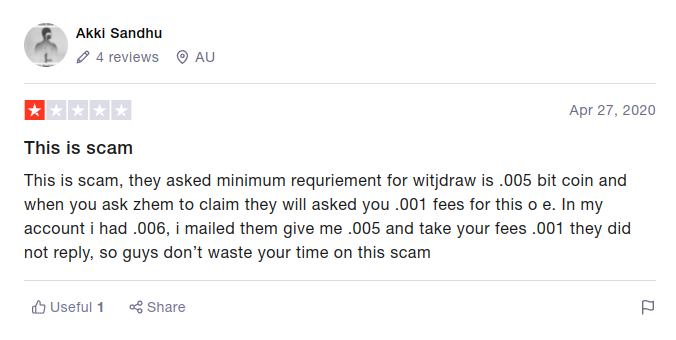
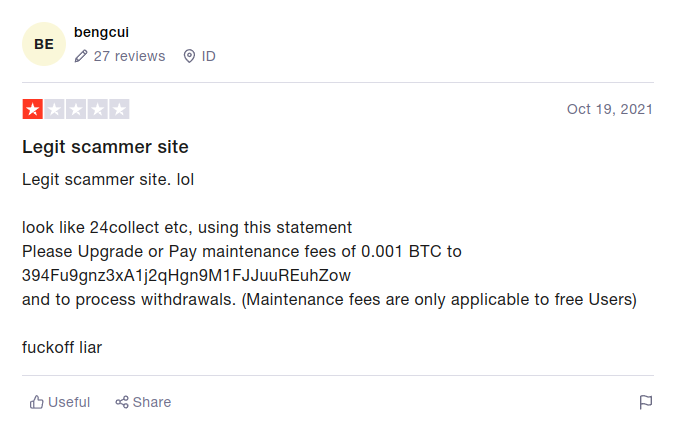
There are multiple reports of fraud associated to the website mostly indicating that customers are ignored when they try to withdraw their funds after paying the associated withdrawal fees. Whilst we don’t want to rely upon third party reports, and I am always wary of these ‘scam or not’ websites, we should take notice of the generally very negative sentiment expressed in these customer reviews, it is a strong indicator that we are dealing with a scam company.
Not Everyone Who Offers Help Is A Friend
Some brief notes on customer review sites - be wary of some of the reviews as these sites are like a watering hole for scammers. Just take these two examples -
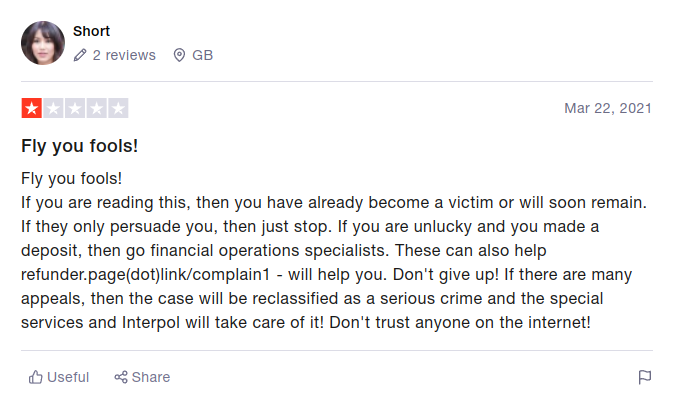
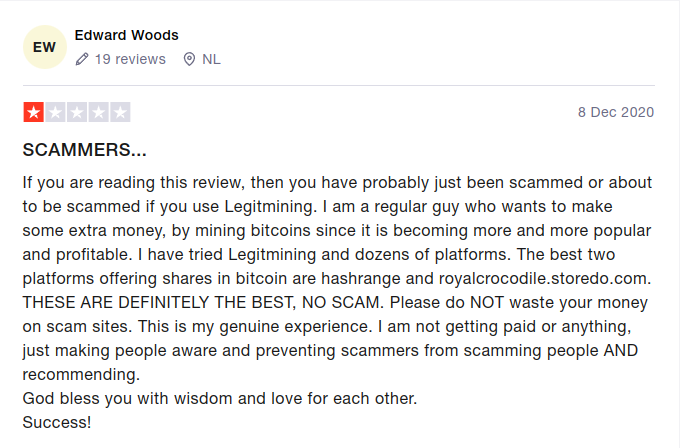
Contrary to the comforting sentiments expressed by the esteemed ‘Short’ I regret to inform you, dear reader, that no matter how much of a fuss you kick up about your stolen bitcoin, Interpol are not going to take the case on. This is just another lowlife scammer looking to exploit desperate people. The only worthwhile information in their review is when they advise you not to trust anyone on the internet, including them, I certainly wouldn’t be visiting the refund site that they recommend.
Would You Like The Moon On A Stick?
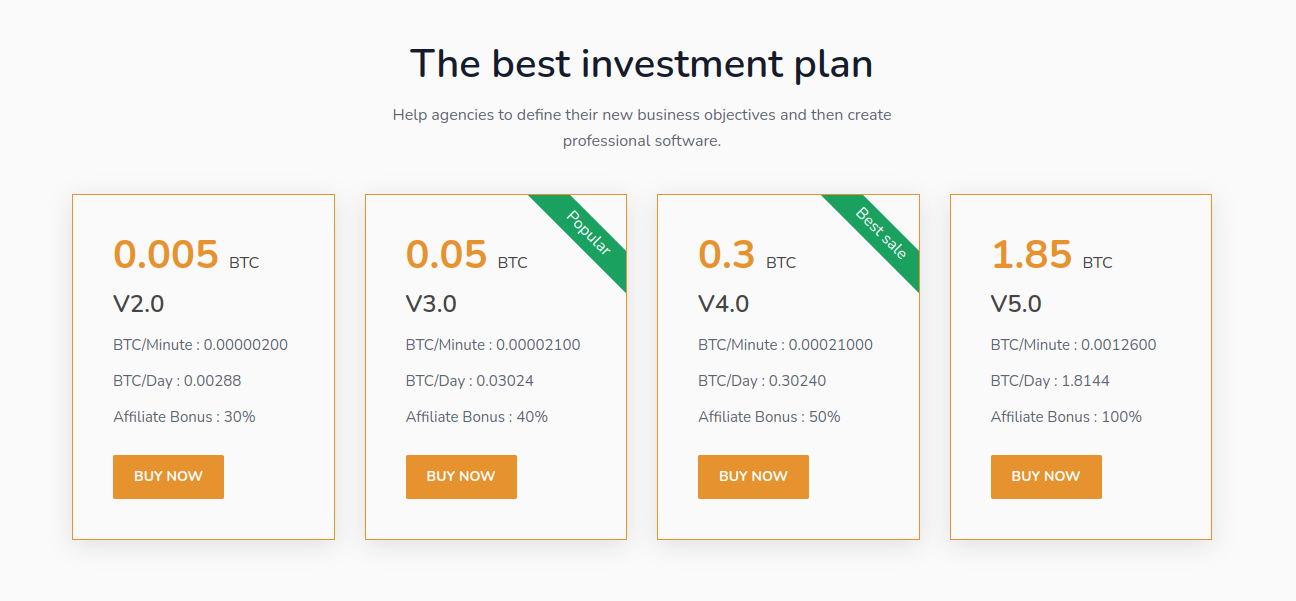
Amongst the bold claims on the site is an eye-catching investment opportunity. A ‘v5.0’ investment plan with legitbitcoin has a claimed payout of 1.8144 BTC per day for an initial investment of 1.85 BTC - that is quite the return on investment. All with low fees, 99.99% server uptime and instant withdrawals, if true it is the deal of the century!
This is a claim so grand that it fits the exact profile of a type of fraud known as a High Yield Investment Program (HYIP). This is a common fraud-type promising astronomical returns from an intially conservative investment that can be presented in a number of ways from investment schemes to binary options trading and in the last few years cryptocurrency investments and mining. The fraudsters use the supposedly huge profits, usually held in an online account visible only via their website, to persuade the victim to invest more cash to make even greater profits. This is usually followed by a long drawn out process of the victim trying to access their profits, being told they have to pay astronomical charges to do so before finally they are completely ignored and the fraudster makes off with all of their money.
As per the title of this series if it seems too good to be true it probably is. Unfortunately many people do fall into the trap set by these fraudsters, whether the victims are motivated by greed, desperation or just the fear of missing out on an opportunity to make lifechanging sums of money. The genuinely huge increase in the value of cryptocurrencies since their inception is manna from heaven for the HYIP fraudsters. They can point to the genuinely staggering profits made by early adopters of cryptocurrencies such as ‘evidence’ of the potential gains to be made through their platforms.
Liars, Liars Everywhere!

Another series of claims, being made on the site are in the form of small pop-ups that gleefully announce when a new customer has signed up to an investment plan.

Unfortunately for the operators of legitmining, that claim falls apart pretty rapidly under even the most basic examination.
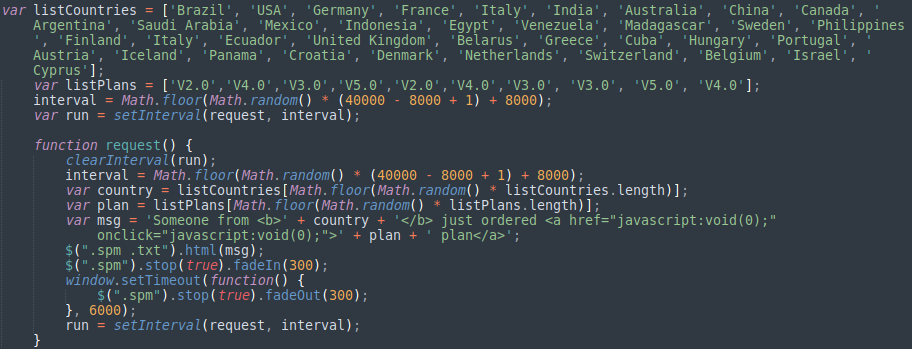
Looking at the source code, which we can examine from our archived site, we see that there is a suspicious looking script that contains a list of countries and plans. I’m no javascript expert but this script appears to be randomly choosing one each of the predefined countries and plans then populating the pop up window with the combination. Rather than being a genuine notification of customer sign-ups it is a simple randomised pop-up script. How very dishonest! If the operators of the site are willing to lie about something as simple as this we are entitled to ask “why are they lying about this?” and “what else are they lying about?”.
Taking the Bait
What happens when we decide to engage a little with the site and follow their prompts to enter a bitcoin address to start mining immediately? If we select an entirely random public bitcoin wallet address from a random transaction on the bitcoin blockchain and enter it into the site what will happen?
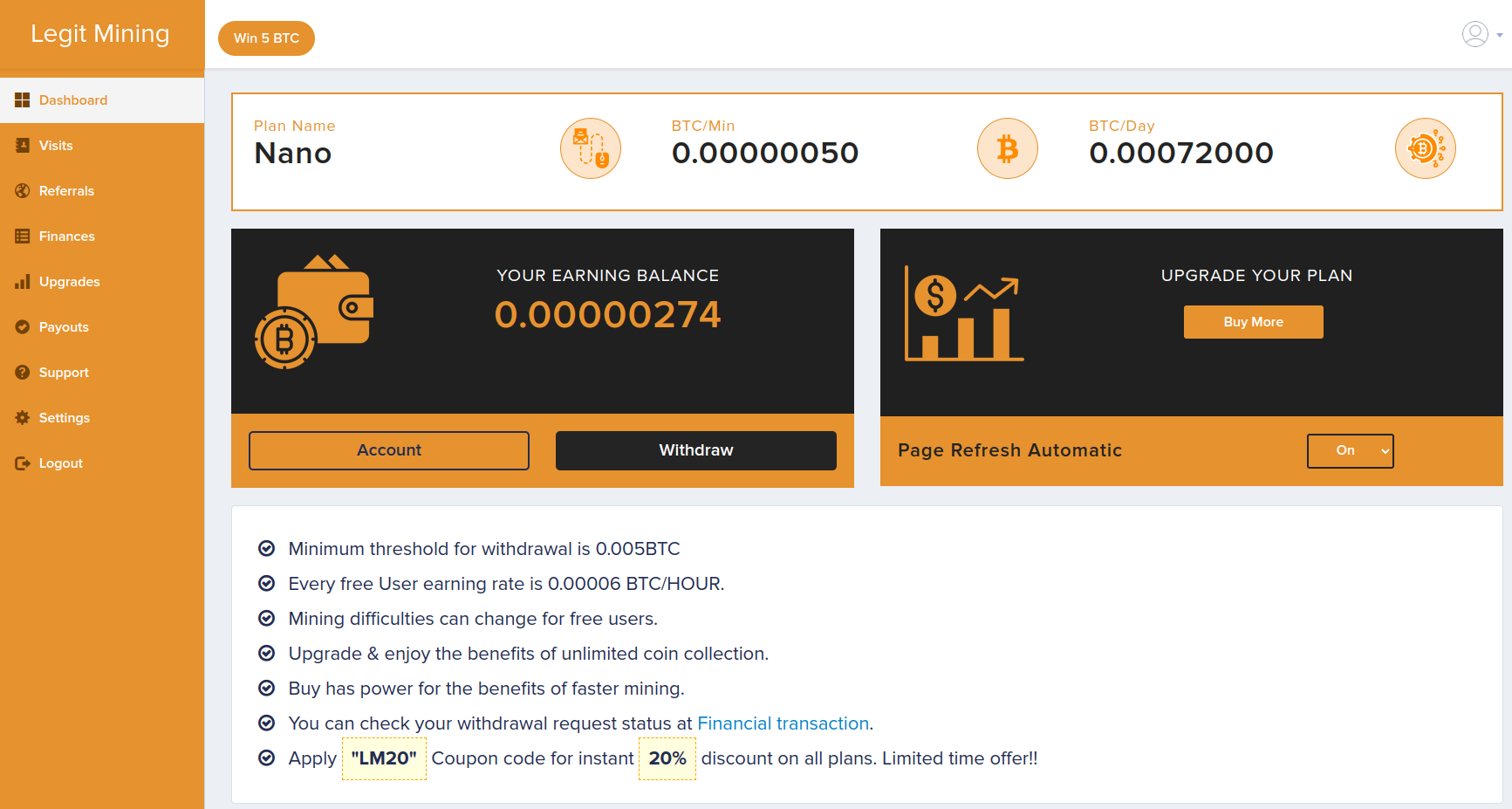
We are transported to an interactive dashboard where bitcoin is accumulating in our account already, we are going to be rich in no time at all!
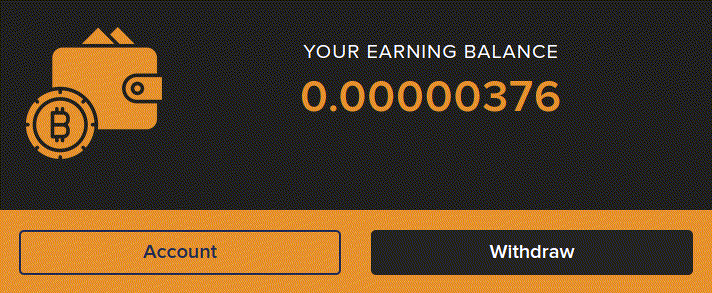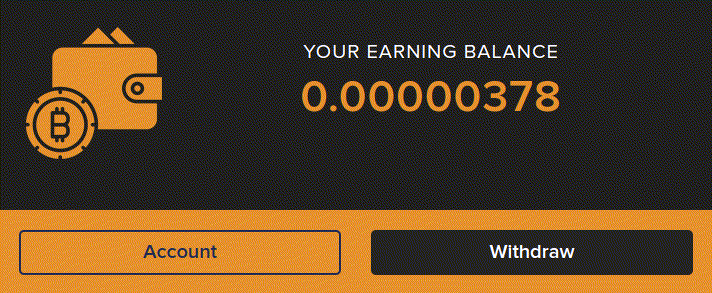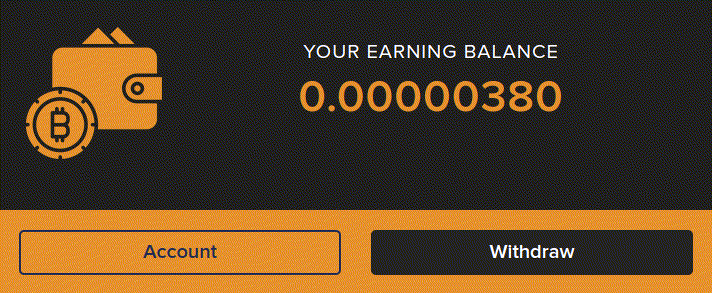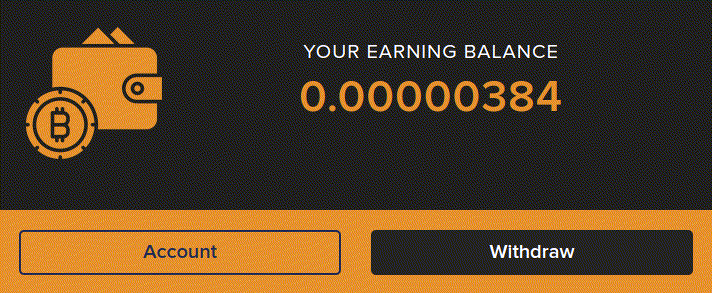
The dashboard indicates that we have to wait until our balance has reached the minimum withdrawal amount of 0.005 BTC (around $200) and then pay a withdrawal fee to access our funds. If we can’t stand to wait then we are helpfully prompted to boost our hash rate by buying extra mining power. All this seems pretty straightforward but there is a major problem. We haven’t created a user account and we haven’t given them any personal details at all other than a random bitcoin public address. This is not how any kind of financial service works and if alarm bells weren’t already ringing they should be pretty deafening by now, something is definitely amiss.
Checking the website code again gives us our answer. The balance ticker is just a simple number counter script embedded in the webpage. There is no connection from the balance being displayed to any outside source, it is complete smoke and mirrors.
In fact if we visit the same page in our archive we can see both the balance script and the pop-up scripts are still running, even though we are not connected to the target site at all.
Some Conclusions
It is hopefully pretty obvious to anyone still reading that the legitmining[.]website is very far from legit and is a front for scamming innocent and somewhat naive people out of their hard-earned money.
You may be thinking that this was all somewhat facetious. I’m sure it would have taken 99% of people reading this article just a few seconds to look at the legitmining[.]website and determine that it is not a genuine bitcoin mining service. However, it is important to be able to back up gut feelings with evidence-based reasoning to support our conclusions. Plus, the lessons we have learned about how the scam operates and which particular techniques of deception are used may help us to answer some of the more difficult questions later on in our investigation.
In the next article in this series we will take a look at pivoting out from the information gained in our initial examination of the target website. This will include looking at the infrastructure that supports the website and using enumeration of that infrastructure to identify linked websites, involved individuals and to get a sense of the scale of this fraudulent operation. It will be a bit more technical but hopefully pretty interesting.
I’d appreciate any (polite) feedback, I have a pretty thick skin so please feel free to leave a comment below or reach out to me on twitter @webjitsu or via email [email protected].